Download PDF
Client Requirement
Malware today are so advanced that they can be programmed to silently absorb information via recording key logging. Customer requested a real time encrypting software to safeguard users applications and computers from malicious software trying to sneak information by recording key press information.
Client’s specific requirements for the software were:
- An interface that allows users to view real time encryption.
- The application must act as defense layer between the kernel and destination app.
- A cryptology technology that can fight the toughest malware.
- Should not be very resource intensive.
- Automatic version control facilities.
- Three different version support – Trial, Pro and Premium.
- Supports maximum applications including browsers and chat applications.
- Should function when a user logs on to Windows locally or logs on to the domain.
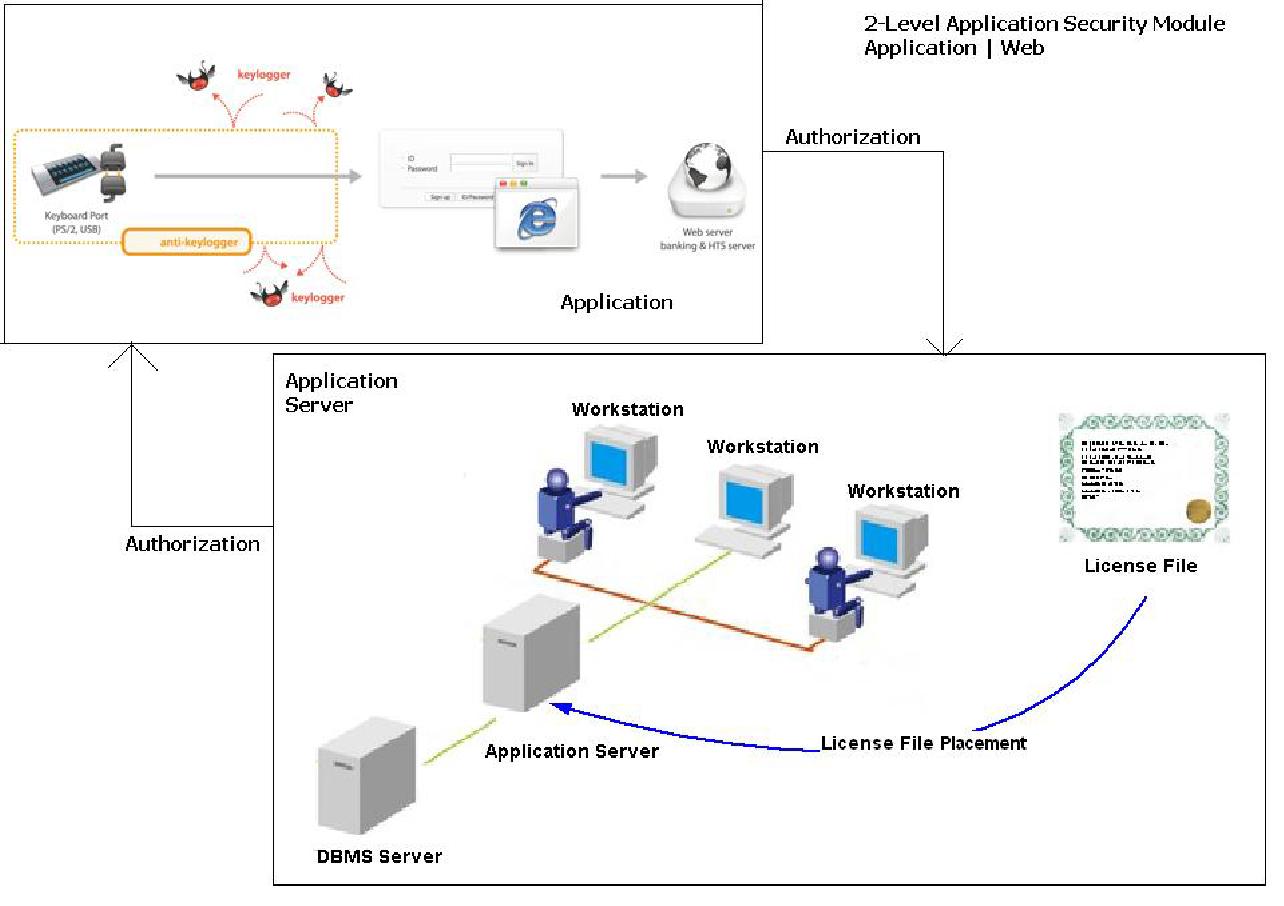
With such stringent requirements, we created a state-of-the-art cryptography software that safeguards user’s applications from malware.This software effectively secures application credentials and defeats key loggers by encrypting key strokes at the keyboard driver level. The software is deeply rooted in the system and key loggers cannot bypass the encryption or decode it.
The application was built to work seamlessly with several authentication programs and along with providing stringent security and privacy methods, also offers easy software installation.
Challenges
The team faced the following challenges:
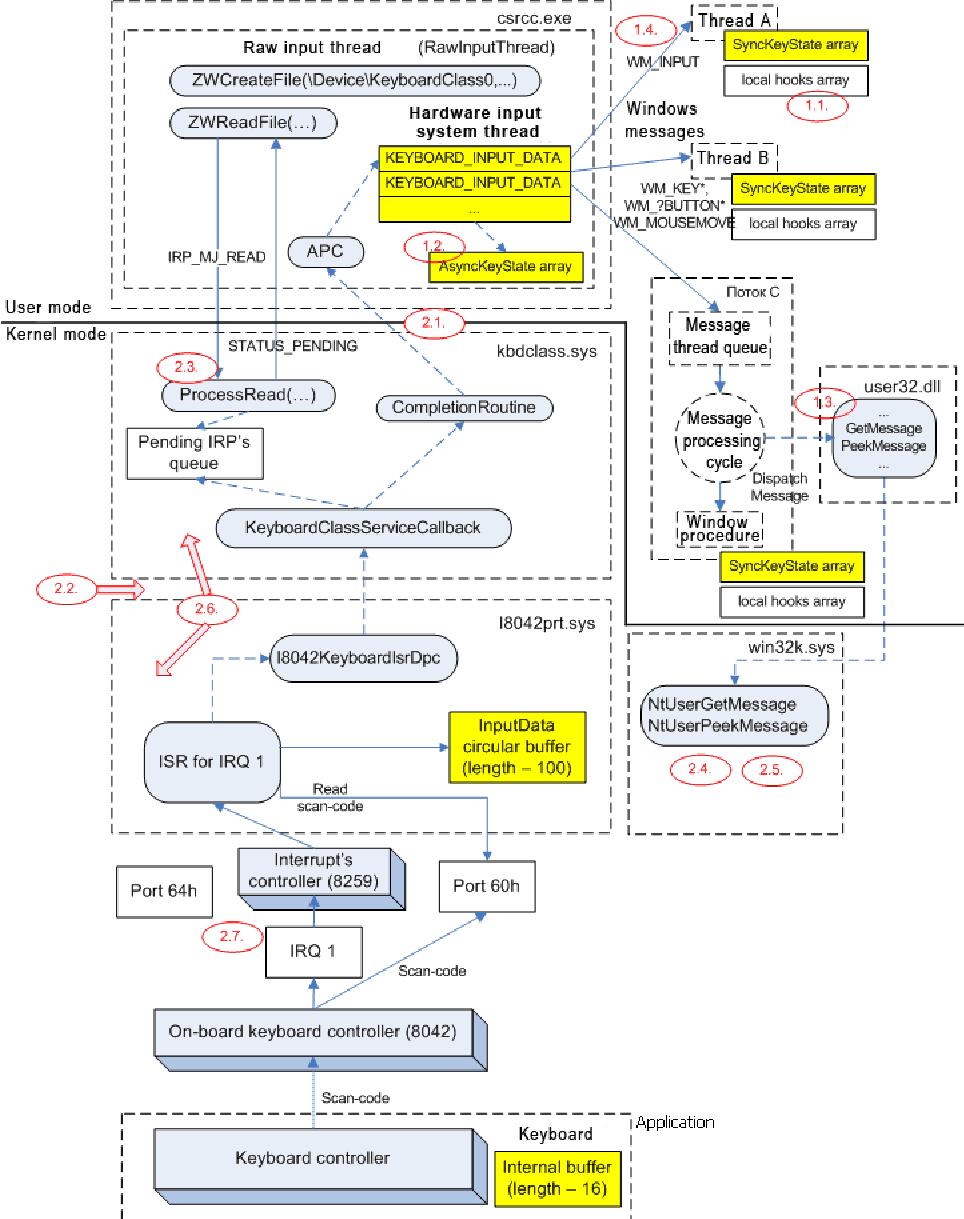
- Developing a driver to support functionalities of the keyboard that support customized encryption for all keystrokes.
- The driver needed to be loaded to memory without any system crashes.
- Driver needed to load at machine start and the driver needed kernel level drive programming.
- Flawless application operation by speeding up at all interfaces and instances.
- Providing the application with a foolproof encryption logic so that the system is non hack able.
- Securing the interaction between server and application.
- Focus on control and making the application work accurately.
Technologies Used
| Operating System & Server Management | Windows OS, Multi-Server Architecture with Staging & Production Environment through Version Controlling releases, Server Optimization, Security & SSL Implementation, Scheduler for Back-ups, Alert Monitoring System Integration, Server Performance Tuning at regular intervals, Software Firewall Configuration & Maintenanc. |
| Development Tools & Environments | Windows DDK, C, Microsoft Visual Studio, VC++, MFC, NSIS, .NetFramework 4.0 etc. |
| Database | MSSQL Database Server, DB Clustering, DB Optimization, Master Slave Replication, Query Optimization, Scheduler for Backups |
Manpower
| Developers | 3 |
| Designers | 1 |
| Quality Assurance Testers | 1 |
Planning
In order to incorporate the numerous features and functionalities, the following development approach was used:
- Usage of high level security and data fetching technology.
- Scheduled research and analysis for desired output for different business verticals.
- High level coding standards followed for managing backup volume. Synchronization with server for the most recent updates was also taken into consideration.
- Current and newly available data had to be in sync for backup.
- The GUI for the software and website needed to be planned.
Driver Architecture
Application Architecture
Development Highlights
The application was made compatible with Windows XP, Vista and Windows 7 operating systems. The entire application was developed with C, assembly language, VC ++ and .Net Framework 4.0. The screens were designed with UML diagram and basic framework integrated for high performance of the application. .Net framework and core graphics were used to develop almost all modules. Wireframes were developed for each dialog box and integrated with UML diagram. Driver module had a complex structure to allow successful communication between driver and user mode applications. Kernel level programming enabled that application to work flawlessly without crashes and memory leaks. A light version installer was used for the application. Over all performance was enhanced by the use of high resolution images with low memory usage. Customized installer was used to enable command line parameters. The application was developed and live in a span of 10 months.



