Security is a crucial constraint for Symfony 2 development. Security is a process in which you can prevent a user from accessing a resource that they shouldn’t. It is a two step process. The first step is Authentication and the second step is authorization.
Security is a crucial constraint for Symfony 2 development. Security is a process in which you can prevent a user from accessing a resource that they shouldn’t. It is a two step process. The first step is Authentication and the second step is authorization.
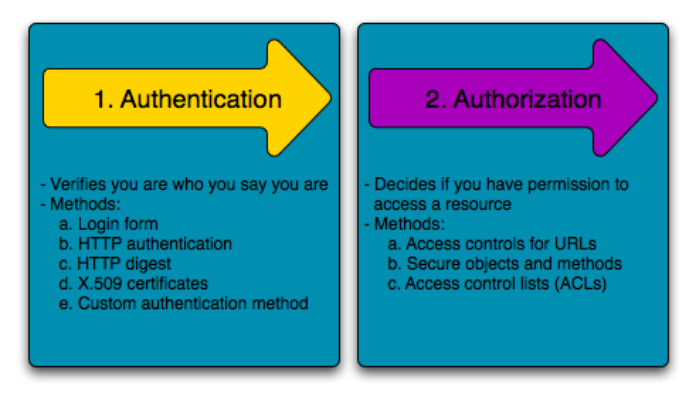
Authentication is the process of identifying a user by requesting the user to submit some sort of identification. Authentication uses methods like Login Form, HTTP Authentication, HTTP Digest, X.509 certificates, Custom Authentication Method etc.
Authorization is the process of identifying whether the user should have access to a given resource or not. Authorization uses methods like Access controls for URLs, Secure Objects and methods, Access Control Lists etc.
Let’s take an example of a Basic HTTP Authentication
To configure security component via application configuration, take a look at the following example for securing any URL matching /admin/* and to ask the users for credentials using basic HTTP authentication.
# app/config/security.yml
security:
firewalls:
secured_area:
pattern: ^/
anonymous: ~
http_basic:
realm: "Secured Demo Area"
access_control:
- { path: ^/admin/, roles: ROLE_ADMIN }
# Include the following line to also secure the /admin path itself
# - { path: ^/admin$, roles: ROLE_ADMIN }
providers:
in_memory:
memory:
users:
ryan: { password: ryanpass, roles: 'ROLE_USER' }
admin: { password: kitten, roles: 'ROLE_ADMIN' }
encoders:
Symfony\Component\Security\Core\User\User: plaintext
PHP
// app/config/security.php
$container->loadFromExtension('security', array(
'firewalls' => array(
'secured_area' => array(
'pattern' => '^/',
'anonymous' => array(),
'http_basic' => array(
'realm' => 'Secured Demo Area',
),
),
),
'access_control' => array(
array('path' => '^/admin/', 'role' => 'ROLE_ADMIN'),
// Include the following line to also secure the /admin path itself
// array('path' => '^/admin$', 'role' => 'ROLE_ADMIN'),
),
'providers' => array(
'in_memory' => array(
'memory' => array(
'users' => array(
'ryan' => array(
'password' => 'ryanpass',
'roles' => 'ROLE_USER',
),
'admin' => array(
'password' => 'kitten',
'roles' => 'ROLE_ADMIN',
),
),
),
),
),
'encoders' => array(
'Symfony\Component\Security\Core\User\User' => 'plaintext',
),
));
This code accomplishes the following
The code has two users, ryan and admin. Basic HTTP authentication prompt is used for authentication and any URL matching /admin/* is secured. Only admin users can access it. Any URLs that do not match this can be accessed by all users.
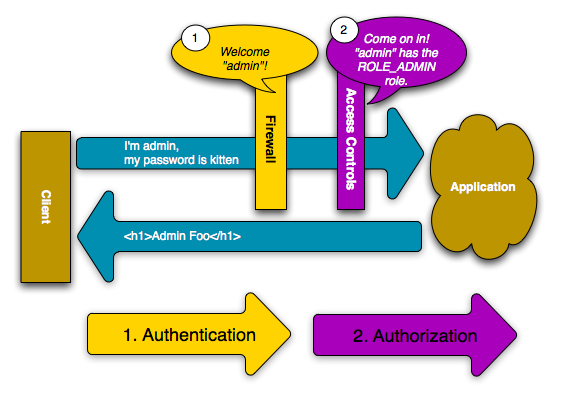
Symfony’s security system works by determining the identity of the user first and then checking to see if that user should have access to a given resource or not
Firewalls (Authentication)
If a user requests a URL that is protected by a firewall, the security system is activated. The firewall checks whether the user needs to be authenticated and sends a response back to the user. In the given example, the pattern(^/) should match every incoming request. The HTTP authentication username and password box is not necessarily displayed for every URL. The firewall allows anonymous users via the anonymous configuration parameter. However, if you remove the anonymous key, the firewall will make it compulsory for the user to always fully authenticate.
Access Control (Authorization)
Whenever a user requests /admin/foo the security process runs differently because the access_control configuration says that any URL that matches the regular expression pattern (i.e. /admin or anything matching /admin/*) required the ROLE_ADMIN role to be assigned. These roles form the basis for authorization and user access.
Initially the firewall does not make any request, but when the access control denies access, the firewall triggers the authentication process. This authentication process depends on the method that you are using. For example, if you have configured the form authentication process, the user will then be redirected to the login page. If HTTP authentication is used, the user is redirected to 401 and the user can then see the user name and password box.
To sum it up…
The security flow uses the following process:
- User requests access to a protected resource.
- The app redirects user to the login form
- User enters his login credentials.
- The user is authenticated by the firewall.
- The original request is retried.